Defense Is Best Offense against Ransomware

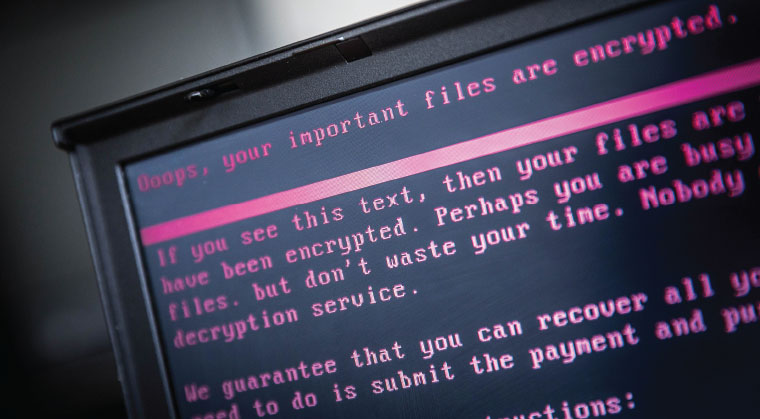
ON THE OFFENSIVE Much of the damage caused by ransomware attacks could be forestalled by timely downloads of Windows updates. But many individuals ignore notifications to download security updates
J ust as some infectious diseases mutate to fight off antibiotics cagy cyber-criminals have developed the tools to modify the viruses and worms they unleash for computer cyber attacks rendering the victims’ computers indefensible.
That was evident during last week’s global ransomware attack known as “Petya” a worldwide threat that crippled tens of thousands of computer systems at banks shipping companies and utilities mainly in the US Europe and Asia.
Petya attacked the same vulnerability in the Microsoft operating system that a previous cyber attack in May known as WannaCry targeted. “The difference is with WannaCry someone found a kill switch to terminate the attack. The attackers have now modified this so there’s no way to decrypt it and files are irretrievable after they’ve been attacked ” said Yair Solow CEO of CyGov an Israeli company whose leading members were intimately involved in the development of Israel’s National Cyber Agency.
The Petya ransomware forced Maersk the world’s largest operator of container ships to close terminals around the world including one in the Port of Los Angeles for three days. It also shut down ATM machines and the decommissioned but still monitored Chernobyl nuclear plant in Ukraine which was forced to move to manual operation.
The cyber attacks are dubbed ransomware because the attackers send a message to the users of the computer explaining that their files are locked and demanding payment through Bitcoin — in this case $300 —to unlock the files.
“From research we’ve done very few people have paid to unencrypt and those who have paid found that they didn’t get their information back ” Solow says.
Much of the damage caused by ransomware attacks could be forestalled by timely downloads of Windows updates. But many individuals ignore notifications to download security updates that include protective patches. Even larger organizations that have cyber budgets and IT teams are often too focused on the technology side to notice other security threats.

“From research we’ve done very few people have paid to unencrypt and those who have found that they didn’t get their information back” —Yair Solow
Solow recommends a holistic cyber strategy that includes the physical protection of buildings that hold servers and computers and collecting intelligence — even on one’s own employees.
“Some 44% of the attacks today are originating from inside an organization” Solow says. “Some are malicious and some are inadvertent but in some cases governments and companies are spending millions of dollars to put up these big walls and they’re not alert to what’s going on inside their own walls.”
There is also no substitute for exercising good judgment by not clicking on a website or e-mail attachment from an unknown or suspicious source.
“There are constant battles with employees to educate them ” Solow says citing the urgency now that ransomware programs once the domain of state-sponsored terrorists are now available for purchase on websites for as little as $39.
“It’s the equivalent of a fighter jet being in the hands of a terrorist group. It gives them the ability to disrupt lives at a very low cost. We hope these attacks will make people take a step back and take a good look in the mirror and hit the reset button before the next cyber 9/11 hits ” Solow said. (Originally featured in Mishpacha Issue 667)
Oops! We could not locate your form.